The digital workplace has undergone a seismic shift. Gone are the days of centralized workforces, replaced by a geographically dispersed landscape of remote and hybrid employees.
While this flexibility empowers businesses and workers alike, it also presents a significant security challenge, ensuring secure access to corporate resources for users outside the traditional network perimeter.
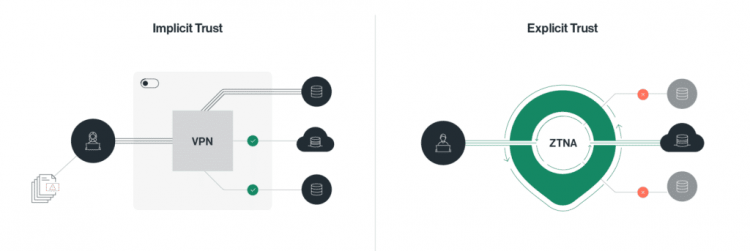
Virtual Private Networks (VPNs) have long been the go-to solution for remote access, but their limitations are becoming increasingly apparent.
The Limitations of Traditional VPNs
VPNs have served businesses well by creating a secure tunnel for remote users to access on-premises resources. However, as the IT landscape shifts towards cloud-based applications and hybrid work models, VPNs struggle to keep pace.
Once authenticated through a VPN, users often gain access to a large portion of the internal network, potentially exposing sensitive data even if they shouldn’t have permission to view it. This inherent trust model creates a significant security risk.
IT teams can take time and effort to manage a growing number of VPN users and connections. Scaling a VPN infrastructure often requires additional hardware and complex configurations, straining resources and hindering agility.
VPNs can introduce latency and hinder application performance, especially for users with unreliable internet connections. This can lead to frustration and reduced productivity for remote workers.
It primarily focuses on creating a secure tunnel, often lacking granular access controls or advanced threat detection capabilities in today’s complex security environment.
Why ZTNA is The Secure Remote Access Game Changer
Zero Trust Network Access (ZTNA) offers a fundamentally different approach to secure remote access. Unlike VPNs, ZTNA operates on the principle of “least privilege.” This means users are granted access only to the specific resources they need for their job functions, and only for the duration required. Here’s how ZTNA addresses the limitations of VPNs:
- Continuous Authorization: ZTNA continuously verifies a user’s identity, device health, and authorization to access specific applications every time they attempt to connect, regardless of location. This eliminates the inherent trust associated with VPNs and minimizes the attack surface.
- Granular Access Control: Provides granular access controls, allowing IT teams to define precisely which applications and resources each user can access. This minimizes the potential damage caused by a security breach and ensures that only authorized users have access to sensitive data.
- Cloud-Native Scalability: Solutions are typically cloud-delivered, offering effortless scalability to accommodate a growing remote workforce. This eliminates the need for complex on-premises infrastructure management.
- Enhanced Performance: ZTNA often utilizes direct connections to cloud applications, bypassing the corporate network entirely. This can significantly improve application performance for remote users.
- Integrated Security Features: ZTNA integrates with existing security tools like multi-factor authentication (MFA) and user behavior analytics (UBA) for advanced threat detection and prevention.
An Easy Ride
Moving from a VPN-based access system to ZTNA requires careful planning and consideration. Implementing ZTNA often requires a cultural shift within the organization, moving away from the traditional “castle-and-moat” security model of VPNs. User education and clear communication are essential for a successful transition. A robust IAM system is crucial for ZTNA to function effectively. This ensures accurate user identification and facilitates the enforcement of granular access controls.
A key aspect of a smooth transition is ensuring ZTNA covers all access points, including web applications, mobile devices, and traditional desktops. Evaluating your existing security infrastructure and potential gaps is essential. This phased approach to ZTNA adoption can minimize disruption and allow for user familiarization.
ZTNA adoption can minimize disruption and allow for user familiarization. Starting with a pilot group of users can help identify and address any potential issues before a wider rollout. Security is an ongoing process. Closely monitor system performance, user behavior, and threat activity after implementing ZTNA. This allows for adjustments to optimize security posture and ensure a seamless user experience.
Summary
The rise of remote work has exposed the limitations of traditional VPNs for secure remote access. While VPNs create a secure tunnel, they often grant users broad access to internal networks, potentially exposing sensitive data if a breach occurs.
Also, managing and scaling VPNs for a growing remote workforce can be cumbersome and resource-intensive. VPNs can also introduce latency and hinder application performance, especially for users with unreliable internet connections.
Zero Trust Network Access (ZTNA) emerges as a more secure and dynamic alternative. Unlike VPNs, ZTNA operates on a “least privilege” principle, continuously verifying user identity, device health, and authorization to access specific applications every time they attempt to connect.